In this post I will be creating a standard access-list to prevent traffic from R0 reaching from reaching the R3 router.
I'll be using the diagram below for my network layout.
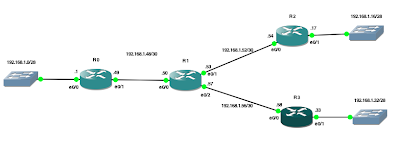
As Standard ACL's can only filter based on the source address they should be placed as near to the destination as possible. Standard access-lists can be numbered from 1-99 or 1300-1999 (expanded range). Standard access-lists can also be named. In this post I'll be using a numbered Standard ACL.
I begin by verifying connectivity before the rule is created.
R0R0#ping r3Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.58, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 4/8/16 msNext I create the standard access-list
R1R1#conf tEnter configuration commands, one per line. End with CNTL/Z.R1(config)#ip access-list standard 1R1(config-std-nacl)#deny host 192.168.1.49 logR1(config-std-nacl)#permit any logR1(config-std-nacl)#exitI have enabled logging so I can see as each statement is hit. There is an implicit deny all statement so none is required in the access-list itself.
I place the access-list as near to the destination as possible. In this case it will be on e0/2 on R1, and it will be outgoing. Placing the list any nearer to R0 would affect traffic to R2.
R1(config)#intR1(config)#interface ethernet 0/2R1(config-if)#ip access-group 1 outR1(config-if)#endI can check the ACL with a show command.
R1#sh ip access-lists 1Standard IP access list 1 10 deny 192.168.1.49 log (0 matches) 20 permit any log (0 matches)I can also check which interface the rule is applied to.
R1#sh ip interface ethernet 0/2Ethernet0/2 is up, line protocol is up Internet address is 192.168.1.57/30 Broadcast address is 255.255.255.255 Address determined by non-volatile memory MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is disabled Multicast reserved groups joined: 224.0.0.9 Outgoing access list is 1 Inbound access list is not set Proxy ARP is enabled Local Proxy ARP is disabled Security level is default Split horizon is enabled ICMP redirects are always sent ICMP unreachables are always sent ICMP mask replies are never sent IP fast switching is enabled IP fast switching on the same interface is disabled IP Flow switching is disabled IP CEF switching is enabled IP CEF Feature Fast switching turbo vector IP multicast fast switching is enabled IP multicast distributed fast switching is disabled IP route-cache flags are Fast, CEF Router Discovery is disabled IP output packet accounting is disabled IP access violation accounting is disabled TCP/IP header compression is disabled RTP/IP header compression is disabled Policy routing is disabled Network address translation is disabled BGP Policy Mapping is disabled WCCP Redirect outbound is disabled WCCP Redirect inbound is disabled WCCP Redirect exclude is disabledFrom the output above I can see that the ACL is applied to the right interface in the right direction. Only one access-list can be applied per interface per direction.
Now I check my pings fail to reach R3 from R0
R0R0#ping r3Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.58, timeout is 2 seconds:U.U.USuccess rate is 0 percent (0/5)Back on R1 I can see the deny statement has been hit.
R1*Mar 1 00:33:33.783: %SEC-6-IPACCESSLOGNP: list 1 denied 0 192.168.1.49 -> 192.168.1.58, 1 packetTo verify that my traffic can still hit R2 I attempt to ping it from R0.
R0R0#ping r2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.54, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 4/12/24 msR2I can also check that traffic from R2 can reach R3.
R2#ping r3Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.58, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 8/8/12 msR1This can be seen hitting the permit statement in the access-list.
*Mar 1 00:42:00.419: %SEC-6-IPACCESSLOGNP: list 1 permitted 0 192.168.1.54 -> 192.168.1.58, 1 packetChecking the access-list again I can see a number of hits.
R1#sh ip access-lists 1 Standard IP access list 1 10 deny 192.168.1.49 log (5 matches) 20 permit any log (5 matches)As R3 is receiving its route updates from R1 it will still know about R0 and how to find it.
R3R3#sh ip routeCodes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static routeGateway of last resort is not set 192.168.1.0/24 is variably subnetted, 6 subnets, 2 masksC 192.168.1.32/28 is directly connected, Ethernet0/1C 192.168.1.56/30 is directly connected, Ethernet0/0R 192.168.1.48/30 [120/1] via 192.168.1.57, 00:00:15, Ethernet0/0R 192.168.1.52/30 [120/1] via 192.168.1.57, 00:00:15, Ethernet0/0R 192.168.1.0/28 [120/2] via 192.168.1.57, 00:00:15, Ethernet0/0R 192.168.1.16/28 [120/2] via 192.168.1.57, 00:00:15, Ethernet0/0However, R3 cannot recieving ping responses from R0 because the echo replies will be blocked by the access-list.
R3#ping r0Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.49, timeout is 2 seconds:.....Success rate is 0 percent (0/5)Using a debug command on R0 I can see the pings hit the router but they cannot get back.
R0R0#debug ip icmpICMP packet debugging is onR0#*Mar 1 00:56:11.823: ICMP: echo reply sent, src 192.168.1.49, dst 192.168.1.58*Mar 1 00:56:11.835: ICMP: dst (192.168.1.49) administratively prohibited unreachable rcv from 192.168.1.50
I finish up by removing the ACL from the interface and the router.
R1
R1(config)#interface ethernet 0/2
R1(config-if)#no ip access-group 1 out
R1(config-if)#exit
R1(config)#no access-list 1
R1(config)#end













